What is phishing?
We take many measures to protect our tech infrastructure from cyber attacks. Besides, awareness level of our employees is at a significant point in cyber security. Because a remarkable amount of cyber attacks are done over employees of a company.

What is ID phishing?
“ID phishing” is the most common kind of cyber attack. These attacks can be many different ways. But all have the only common purpose. Trying to capture your vulnerable information such as identity, credit card or username. Let’s get started to attacking kinds and definitions with phishing.

How did I understood the phishing attack?
In these kind of attacks, the attacker pretends like a real company to capture your login information. Directs you to a fake web page to seize your account information by sending an e-mail. Subsequently it seized the information you entered, then directs you to a real page. The information that the attacker captured, enables it to harm you or the company you work for.

Spear
It’s a more complicated phishing attack that includes specified information which enables the attacker look like a legitimate source. It is targeted to make you click on the link or extension by using your name, phone number or company information.

Whaling
It’s a popular method that enables you to transfer money to a hacker or send your vulnerable information through e-mail by pretending like a real company executive or a department. They look like an ordinary e-mail similar to Multinet (sistembilgi@abc.com.tr or sistembilgi@abc.com.tr like) from a senior executive or a department of a company and request your vulnerable information like (usernames and passwords)
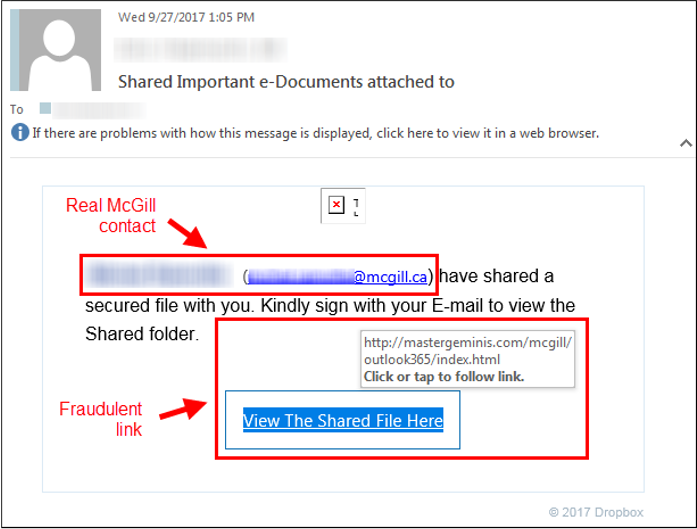
Sharepoint Document Phishing
You might receive an e-mail which looks like from a file sharing site like Sharepoint and notifies you that a document was shared. The link provides in these e-mails takes you to a fake entry page that pretends a real entry page and will steal your accounts ID information.
What should we do as a precaution for phishing attacks?
Please consider the warning warnings below to avoid the attacks we wrote above:
- Do not click on the links and extensions that are from unknown mail addresses. Especially be careful to .zip, other compressed or .exe file types.
- Do not reply to e-mails request your personal information.
- Be careful against to e-mail addresses that use suspicious or misleading names.
- Examine the URL’s sent carefully to make sure they are correct.
- Do not give your personal information to suspicious or unknown websites.
- Do not try to open a document that you don’t expect to receive.
- Be careful while you open an extension or clicking links, if you received a warning e-mail that indicates it is from an out source.
- Turn Back
- 4 min reading
-
Securvent